If you want the Aptify site to be accessible from any computer on the local network and from remote computers using a VPN connection, you can deploy the website using the local intranet approach. This section includes the following:
Authentication
Authentication Recommendations
In Aptify 5.5.1, Aptify recommends using Basic Authentication with SSL. This is the default setting when Aptify is installed.
In Aptify 5.5.2 and later, the default authentication method when Aptify is installed is Anonymous Authentication with SSL, but you can choose other authentication methods. See Choosing an Authentication Method for more details.
In Aptify 5.5.1, when deploying the Aptify site as an internal site, the site can be configured to use either Basic or Integrated Security (Windows Authentication). In this case, the website can be configured to use Integrated Security in this mode because the client will have access to the domain controller. (Note that using Integrated Security requires the domain controller to be accessible to the client browser.) Keep in mind the following when decided which authentication method to choose in an Aptify 5.5.1 implementation:
- When using Windows Authentication, constrained delegation must be configured from the web server to the database server, but it can be limited to the Kerberos protocol only. See Aptify Site and Network Delegation for information on configuring constrained delegation.
- When using Basic Authentication, the site must be secured with SSL to protect login credentials.
In Aptify 5,5,1, when deploying the Aptify site as an internal site, the site can be configured to use Anonymous Authentication (the default method or Basic or Windows Authentication if your organization requires authentication through IIS, for example when using single sign‐on). In this case, the website can be configured to use Integrated Security in this mode because the interface will have access to the domain controller. (Note that using Integrated Security requires the domain controller to be accessible to the web browser.) Keep in mind the following when decided which authentication method to choose:
- When using the default Anonymous Authentication, the site must be secured with SSL to protect login credentials.
- When using Windows Authentication, constrained delegation must be configured from the web server to the database server, but it can be limited to the Kerberos protocol only. See Aptify Site and Network Delegation for information on configuring constrained delegation.
- When using Basic Authentication, the site must be secured with SSL to protect login credentials.
Aptify Site and Network Delegation
When using Windows Authentication, Aptify uses impersonation to pass a user's login credentials from the web server to the database server. When the web server and database server reside on different computers on the network, a network administrator needs to enable delegation to allow the web server to pass the impersonated credentials to the database server.
Note for Aptify 5.5.2 Implementations
In Aptify 5.5.2 and later, when using Basic or Anonymous Authentication, setting up network delegation may not be required.
Note
Active Directory must be replicated after delegation is configured to propagate the changes to all domain controllers.
Delegation is configured by a network administrator using the Active Directory Users and Computers interface, which is available as an Administrative Tool on the domain controller. Note that Aptify requires that you configure constrained delegation, which is available for Windows 2003 domains and higher.
The Aptify web interface does not currently support the authentication of users from multiple domains from a single website. If your environment supports users in multiple domains, contact Aptify Technical Support for assistance.
When deploying the Aptify site on the local Intranet, the Kerberos protocol is used for authentication. When deploying the Aptify site on the public Internet, any protocol may be used, including Kerberos. In order to use Kerberos authentication securely, services on both the database server and the web server must be mapped to service principal name (SPN) in Active Directory. This ensures that the accounts that run these services can be uniquely identified for mutual authentication with Kerberos. By default, when installing Microsoft SQL Server 2008 (and higher) is installed, the account that is specified to run the database service is mapped to an SPN automatically. However, when IIS 7 is installed on the web server, the account that is used to run the HTTP service is not automatically mapped to a SPN. Therefore, prior to configuring delegation, an account that has the proper permissions to run the HTTP service on the web server must be mapped to a SPN in Active Directory. See Configuring Service Principal Names for the Web Server for more details.
This section contains the following:
Note
Refer to Microsoft's documentation for more information on configuring delegation on your network. For an introduction to delegation in Windows Server environments, see the "How to Configure the Server to be Trusted for Delegation" article at:
http://technet.microsoft.com/en-us/library/ee675779.aspx
Also, for information on using constrained delegation with ASP.NET applications, such as Aptify, see "How To: Use Protocol Transition and Constrained Delegation in ASP.NET 2.0" at: http://msdn2.microsoft.com/en-us/library/ms998355.aspx
Configuring Service Principal Names for the Web Server
IMPORTANT
Check with your Network Administrator if you have any questions about how your network is designed. Failure to do so may results in improperly configured SPN mappings.
In order to use Kerberos authentication securely, services on both the database server and the web server must be mapped to a SPN in Active Directory. This mapping is taken care of by default on the database server. However, by default, when installing IIS, the HTTP service is not mapped to a SPN.
Follow the steps to use the SETSPN utility to create the necessary SPNs for the Aptify web server (these steps are based on a Windows Server 2008 system):
- Log in to the domain controller using a domain administrator account.
- You can run the SETSPN from any Windows computer that supports the utility. However, note that the account that is currently logged into the location computer must be a domain administrator.
- You can run the SETSPN from any Windows computer that supports the utility. However, note that the account that is currently logged into the location computer must be a domain administrator.
- Launch a Command Prompt window.
- Run the following command, replacing WebServerName with the domain name of your web server.
SETSPN -L [WebServerName]
- Displayed is a list of registered SPNs for the web server. Verify whether or not there is a registered SPN for the HTTP service with the port that you are using for your AWA site. If there is a HTTP service entry, it should look similar to below. Note that there may be more than one entry if the web server's NetBIOS name and fully qualified domain name (FQDN) are not the same:
- HTTP/[WebServerName.your.domain][:NonDefaultPort]
- If the HTTP services uses the default port 80, the port preceded by a colon will not be displayed. Only non-default ports are appended to the SPN.
- If a registered SPN is not listed for HTTP service, you need to map a SPN for both the web server's NetBIOS and fully qualified names (per Microsoft best practices). The web server will be used as the account to run the HTTP service. If a SPN for the HTTP is displayed, go to the next step.
- Add a SPN for NETBIOS name of the web server using the following command. Replace :[NonDefaultPort] with a blank value (if using default port 80) or the port you are using for your AWA site. Replace [DOMAIN/WebServerName] with the NETBIOS name of the web server (this will be the account used to run the HTTP service).
SETSPN -A HTTP/[WebServerName][:NonDefaultPort] [DOMAIN/WebServerName or Domain User]- By default, the AWA site is installed under the Default website directory and uses the default port 80 (unless changed by an website administrator). In this case, you do not have to specify the port. You can simply add the SPN as SETSPN -A HTTP/[WebServerName] [DOMAIN\WebServerName or DomainAdmin].
- Note that even if you specify port 80, when displaying the list of SPNs, port 80 will not be appended to the SPN for the HTTP service.
- Add a SPN for fully qualified domain name (FQDN) of the web server using the following command. Replace :[NonDefaultPort] with a blank value (if using default port 80) or the port you are using for your AWA site. Replace [DOMAIN/WebServerName] with the fully qualified name of the web server (this will be the account used to run the HTTP service).
SETSPN -A HTTP/[WebServerFullyQualifiedName][:NonDefaultPort] [DOMAIN/WebServerName]
- By default, the AWA site is installed under the Default website directory and uses the default port 80 (unless changed by an website administrator). In this case, you do not have to specify the port. You can simply add the SPN as SETSPN -A HTTP/[WebServerName] [DOMAIN\WebServerName or DomainAdmin].
- Note that even if you specify port 80, when displaying the list of SPNs, port 80 will not be appended to the SPN for the HTTP service.
- Add a SPN for NETBIOS name of the web server using the following command. Replace :[NonDefaultPort] with a blank value (if using default port 80) or the port you are using for your AWA site. Replace [DOMAIN/WebServerName] with the NETBIOS name of the web server (this will be the account used to run the HTTP service).
- If a registered SPN does exist for the HTTP service; you have two options. You can update the existing SPN or remove and re-add a new SPN specifying the name of the web server as the account. Aptify recommends removing and then re-adding the SPN to ensure that duplicate SPNs are not created.
To remove the existing SPN (or SPNs if the NetBIOS name and fully qualified name are not the same and have be specified separately) use the following command(s):
SETSPN - D HTTP/[WebServerNetBIOSName][:NonDefaultPort] [DOMAIN/WebServerName or Domain Admin User]
SETSPN -D HTTP/[WebServerFullyQualifiedName][:NonDefaultPort] [DOMAIN/WebServerName or Domain Admin User]- Note that if the port of the existing SPN is the default port 80. The port will not be appended to the SPN.
SETSPN -A HTTP/[WebServerNetBIOSName][:NonDefaultPort] [DOMAIN/WebServerName]- By default, the AWA site is installed under the Default website directory and uses the default port 80 (unless changed by an website administrator). In this case, you do not have to specify the port. You can simply add the SPN as SETSPN -A HTTP/[WebServerName] [DOMAIN\WebServerName or DomainAdmin].
- Note that even if you specify port 80, when displaying the list of SPNs, port 80 will not be appended to the SPN for the HTTP service.
SETSPN -A HTTP/[WebServerFullyQualifiedName][:NonDefaultPort] [DOMAIN/WebServerName or Domain Admin User]- By default, the AWA site is installed under the Default website directory and uses the default port 80 (unless changed by an website administrator). In this case, you do not have to specify the port. You can simply add the SPN as SETSPN -A HTTP/[WebServerName] [DOMAIN\WebServerName or DomainAdmin].
- Note that even if you specify port 80, when displaying the list of SPNs, port 80 will not be appended to the SPN for the HTTP service.
- Note that if the port of the existing SPN is the default port 80. The port will not be appended to the SPN.
- After the appropriate SPNs have been added or modified, run the following command again to verify the HTTP services were added correctly to the registered list of SPNs for the web server. Replace WebServerName with the domain name of your web server.
SETSPN -L [WebServerName]Note
For more information about how to implement Kerberos authentication in a double-hop environment, see the resource below. Note that this webcast is for Windows 2003 Server, however, the principals are the same for Windows 2008 and Windows 7.
Enabling Constrained Delegation
Note
Active Directory must be replicated after delegation is configured to propagate the changes to all domain controllers.
Follow these general steps to enable constrained delegation between the web server and the database server for the MSSQLSvc service (these steps are based on a Windows Server 2008 system):
- Log in to the domain controller using an administrator account.
- Open the Active Directory Users and Computers dialog from Start > Administrative Tools.
- Locate the web server in the list of network computers.
- Right-click the web server entry and select Properties from the pop-up menu to open its Properties dialog.
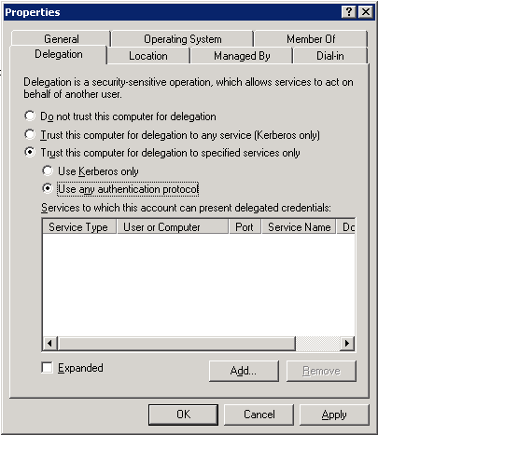
- Click the Delegation tab.
- Select the Trust this computer for delegation to specified services only option to enable constrained delegation.
- Select the Use any authentication protocol sub-option.
- If deploying the Aptify site on the local Intranet, you can also select the Use Kerberos only option. If deploying the Aptify site on the public Internet, you must choose the Use any authentication protocol option.
- See Deploying the Aptify Site as a Publicly Accessible Website and Aptify Site and Network Delegation for more information.
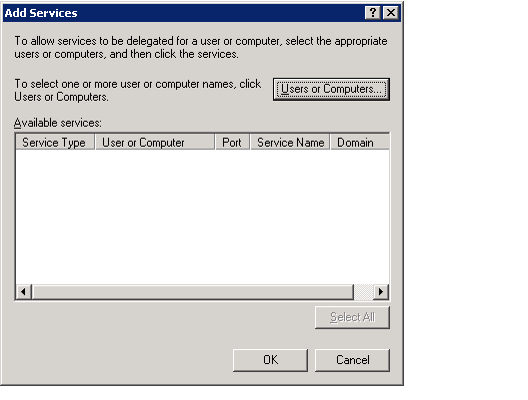
- Click the Add... button to open the Add Services dialog.
- Click the Users or Computers... button and enter the database server (if running under the Local System account) or the custom domain account that is running SQL Server on the database server.
- Whether your SQL server is running under Local System or a custom domain account depends on how your organization has installed SQL Server 2008 on your database server. See the Microsoft SQL Server 2008 Books Online for more information.
- If your organization is using a custom domain account to run SQL Server, keep in mind that you need a service principal name. See "How To: Use Protocol Transition and Constrained Delegation in ASP.NET 2.0" at http://msdn2.microsoft.com/en-us/library/ms998355.aspx for details.
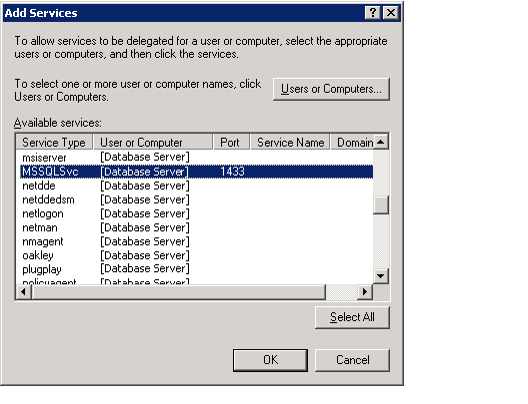
- Select MSSQLSvc from the available service types for the database server or domain account.
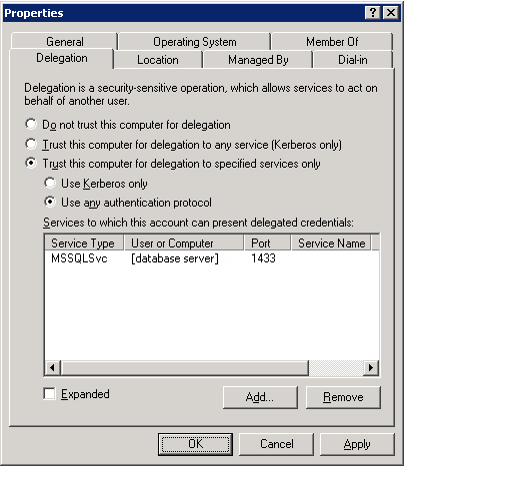
- Click OK to close the Add Services dialog and return to the Properties dialog for the web server.
- Click Apply and OK to save your changes and close the Properties dialog.
- Close the Active Directory Users and Computers dialog.