Introduction
SAML (Security Assertion Markup Language) 2.0 SSO (Single Sign-On) minimizes the number of times a user has to login to various websites. It does this by having the user manually login to one site (called the identity provider or IDP) and then automatically logs the user into one or more other sites (called service providers or SPs), without having to provide credentials. A trust relationship must exist between the identity provider and the service providers, such that the Service providers trust that the identity provider has authenticated the user. SAML 2.0 supports two single sign-on flows:
...
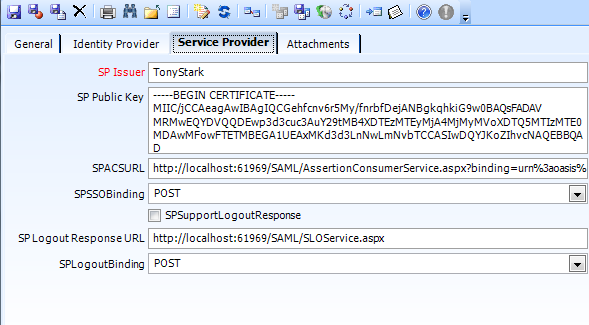
- SPIssuer - nvarchar(100) - required - The value of the Issuer element in SAML messages from the SP.
- SPPublicKey - nvarchar(max) - if this record is for an IDP, this is the X509 certificate to use for validating messages from the SP.
- SPACSURL - nvarchar(200) - if this record is for an IDP, this is the location the assertion will be delivered to when authentication is successful.
- SPSSOBinding - nvarchar(10) - POST or GET - the HTTP protocol the assertion should be delivered on.
- SPSupportLogoutResponse - bit - if true and this record is for an IDP, the IDP will generate a LogoutResponse message.
- SPLogoutResponseURL - nvarchar(200) - the location the LogoutResponse message should be delivered to
- SPLogoutBinding - nvarchar(10) - POST or GET - the HTTP protocol the LogoutResponse message should be delivered on.
Use below Public Key:
-----BEGIN CERTIFICATE-----
...
-----END CERTIFICATE-----
4. Dump sp.pfx file into your website hosting path.
| Info | ||
|---|---|---|
| ||
Following fields are not required:
|
...
Setting up Certificates/Keys
IDP Side:
Dump a .pfx certificate file in some folderRefer idp.cer certificate file and copy it into your website hosting path, specify the full path of the Private Key File in the SAML configuration record under General Tab. The corresponding password should be updated in the Private Key Password field in SAML record.
...
Ideally, for SAML to work between e-Business 6.0 and classic controls on .net based CMS like Sitefinity, the CMS has to be SAML enabled, should be able to send/receive SAML messages. Sitefinity should use any SAML SP plugin or , or we need to code for making the CMS SAML enabled. As of now, as a part of POC for SSO between classic and e-Business 6.0, we have used 2 Login, which means we login to both systems together.
...