Deploying the Aptify Site as a Publicly Accessible Website within a DMZ
If you want Aptify to be accessible from any computer on the Internet without requiring a VPN connection, you can deploy the website using the publicly accessible approach.
See the following sections:
Authentication
Authentication Recommendations
In Aptify 6.0, the default authentication method when Aptify is installed is Anonymous Authentication with SSL, but you can choose other authentication methods. See Choosing an Authentication Method for more details.
In Aptify 6.0, when deploying Aptify publicly, the website should be configured to use Anonymous Authentication (or Basic Authentication if your implementation requires authentication through Microsoft IIS, for example, when using single sign-on). Using a website's Integrated Security (Windows Authentication) option is not recommended in this case because the Integrated Security requires the domain controller to be exposed to the client making the request.
Anonymous Authentication and Basic Authentication passes user name and password information (as well as the token that is generated when the credentials are passed) in clear text, the site must be secured with SSL to protect login credentials.
Moving the Aptify Web Server to a DMZ
Moving the Aptify web server into the DMZ should be performed by your organization's IT team. Refer to Microsoft's online help for Internet Information Services (IIS) for more information on how to configure a web server in a DMZ.
If you want the Aptify web server to be located within a demilitarized zone (DMZ) in your network, Aptify recommends that you install, configure, and test the Aptify web server inside your firewall before moving it into the DMZ.
Once the web server has been added to the DMZ, ensure the following:
The web server is a member of the domain.
Your web server must be joined to the proper domain to allow users to authenticate with Active Directory.
The Domain Name System (DNS) settings are correct and the appropriate ports are opened.
The Aptify web interface does not currently support the authentication of users from multiple domains from a single website. If your environment supports users in multiple domains, contact Aptify Technical Support for assistance.
The database server is accessible from the web server.
One way to test that the database server is accessible from the web server is to launch the Aptify Desktop client from the web server connecting to the database server. If the Desktop client can be launched successfully, the database is accessible.
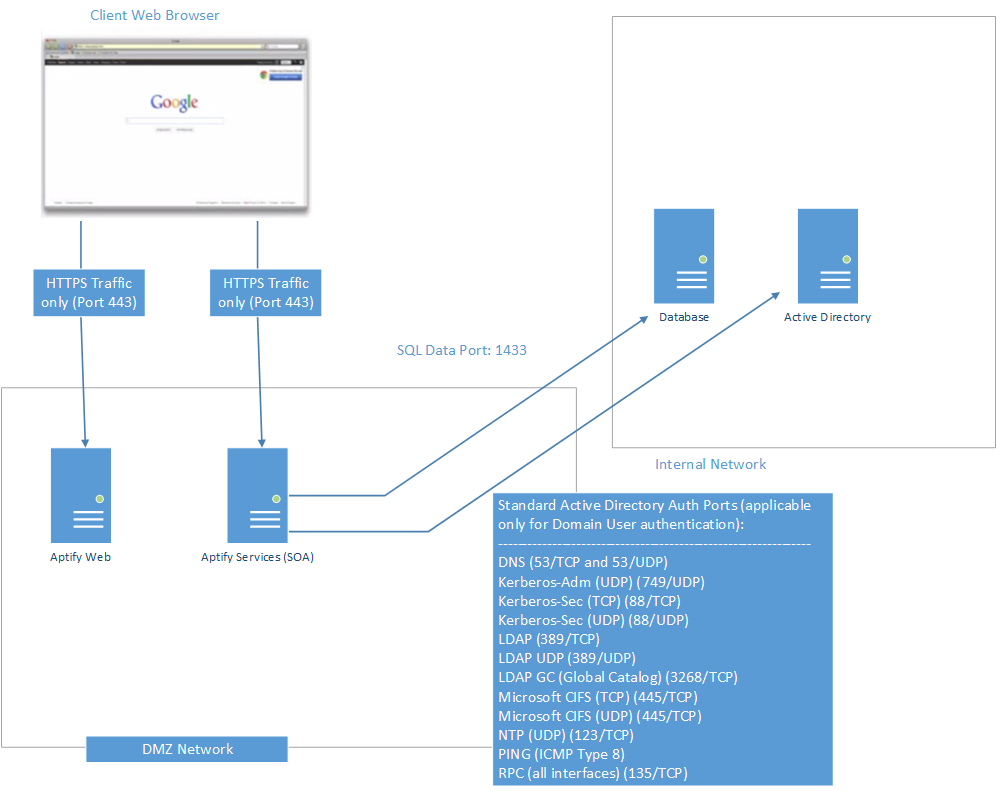
An example Aptify web server deployment in a DMZ is illustrated in the following figure:
Aptify has tested login authentication for domain users in the illustrated deployment using the following scenarios:
Test scenario 1: All domain authentication ports to the domain controller are blocked and all SQL traffic is blocked to the database server. The result was that the login fails, and the traffic destined for both SQL and domain controller is not received by the respective servers. The login fails due to domain authentication not succeeding.
Test scenario 2: All domain authentication ports to domain controller are blocked, and SQL traffic is allowed to the database server. The result was that the login fails, some traffic is received by SQL server, and traffic is not received at the domain controller. The login fails due to domain authentication not succeeding.
Test scenario 3: Domain authentication ports to the domain controller are allowed, and SQL traffic is allowed to the database server. The result was that the login succeeds, and traffic destined for the domain controller and SQL server is received by the respective servers. The login succeeds because the web server is able to create a local login authentication as the domain user logging into Aptify web.
Test scenario 4: Domain authentication ports to the domain controller are blocked, and SQL traffic is allowed to the database server. The result was that the login succeeded, but it takes longer to log in, SQL traffic is received by the SQL server, and traffic going to the domain controller is not received by the domain controller. The login succeeds because the web server has cached the local login for the domain user and is using that to authenticate to the database. This login process takes 15 to 20 seconds longer, because the web server is trying to complete the domain authentication before reverting to cached credentials.
Test scenario 5: All domain authentication ports to the domain controller are blocked, and all SQL traffic is blocked to the database server. The result was that the login fails, and traffic from the web server destined for the domain controller and SQL server is not received by the respective servers. The login fails because while the web server is using cached credentials as in scenario 4, it cannot send cached domain authentication token to the SQL server.
The domain authentication ports used in the example deployment illustrated above are required for Aptify web Active Directory authentication.
Once these steps are complete, connect to the Aptify web interface as before and confirm that the website loads as expected.
Copyright © 2014-2019 Aptify - Confidential and Proprietary